“Passkey” is a mechanism that allows you to log into various websites without passwords, major technology companies such as Apple, Google and MicrosoftPromote useWork.However, if used incorrectlyYubikiWilliam Brown, who created Rust’s WebAuthn library, warns that hardware authentication devices such as Hardware will become unusable.
First year blog
https://fy.blackhats.net.au/blog/2023-02-02-how-hype-will-turn-your-security-key-into-junk/
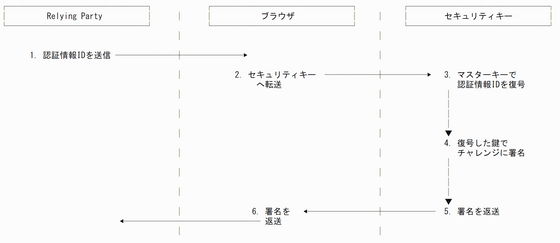
There are two passkey authentication mechanisms: a method that does not store the key on the client side, and a method that stores the key on the client side. If you do not store the key on the client side, generate the key used for authentication in advance, encrypt it with the master key of the security key, and send it to the “Relying Party (RP)”, which is the party that uses the authentication information. At the time of authentication, as shown in the figure below, a key is extracted from the authentication information ID sent by the RP, and a random number called “challenge” is signed to prove the user’s legitimacy.
A key stored on the service side as described above is also called a “non-resident key” or “non-discoverable credential”. Since only the master key is stored in the security key, there is no problem even if you create a large number of accounts. However, it is necessary to enter the ID first so that the appropriate authentication information ID is transmitted during authentication.
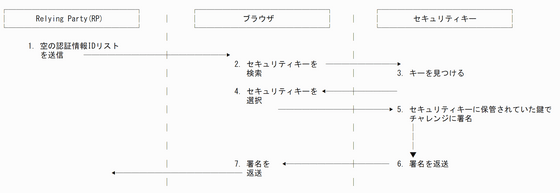
On the other hand, with the client-side key storage method, the authentication step specifies a key stored in the security key rather than decrypting the credential identifier and signing the challenge with that key to prove legitimacy.
By storing the key on the client side, it is possible to eliminate the need to enter not only the password but also the ID, but it is necessary to secure the storage space for the key. According to Mr. Brown, key storage space is very valuable in hardware authentication devices. YubiKeys, for example, can only store 20 to 32 keys.
An additional complication arises with support for client-to-authentication protocols (CTAP) versions and specifications for communication between clients and hardware authenticators. If the hardware authentication device supports CTAP2.1PRE or CTAP2.1, it is possible to update or delete the key stored inside, but in the case of the hardware authentication device of the CTAP2.0 specification, it is impossible to change or delete the key once it is saved.
So, if you store the wrong key, you either give up space for that key or reset the entire device, but a full device reset changes the master key and all credentials associated with that device won’t work anymore.
Big tech companies like Apple, Google, and Microsoft are promoting their useBy doing this, the use of passkeys is widespread, but this method of storing keys on the client side has become mainstream because of the advantage of ‘you don’t even have to enter a username or ID’, and for hardware authentication there is a risk of running out of hardware capacity, notes Mr. Brown. Mr. Brown’s password manager stores passwords for over 150 sites, and if all sites support passkeys, Mr. Brown will need to purchase 5 additional YubiKeys. Moreover, it is necessary to replace it with the YubiKey that corresponds to each site that is authenticated, which makes it difficult to say that it can be used.
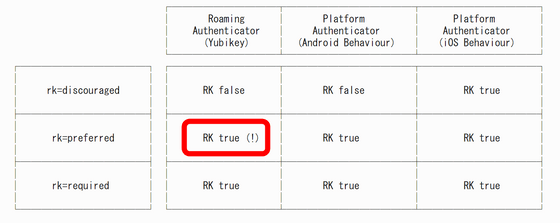
There is no problem with key storage on the client side because the storage limit is loose in passkeys using smartphones. I would like to use it correctly depending on the client, but in the specification at the time of writing, the request level when the authorized party (RP) wants to use the “Resident Key (RK)” method, which stores the key on the client side, is divided into three stages.
Until the above issue is resolved, specifying “rk=disouraged” is the next best thing. It is also stated that one possible solution is to require hardware authentication devices to secure storage as FIDO can store thousands of keys.
Copy the title and URL of this article

“Travel maven. Beer expert. Subtly charming alcohol fan. Internet junkie. Avid bacon scholar.”




More Stories
The Snipping Tool supports inserting emojis and discovering and reading QR codes. The measuring stick is back – Window Jungle
We will be bringing the THINKLET wearable to the “KAMITOHITO INVITATIONAL 2024”, an invitation-only voluntary tournament for Pokemon card games – PHILE WEB
Summary of exciting features in Android 15 beta |