The current malicious activity is a reminder of the importance and vitality of premium accounts, possibly more than the company data itself. Several sessions of the 2020 Gartner Security and Risk Management Summit in mid-September focused on the importance of superior account management Electronic security. In one, titled “Outlook for Identity and Access Management,” David Mahdi, the company’s chief research director, explains what a successful Identity and Access Management (IAM) program looks like in 2020. In particular, on the program, those privileged accounts ( PAM).
The article continues below

As part of his presentation, David Mahdi particularly looked at the conflict between speed and accuracy in a crisis situation: when it comes to responding immediately to a crisis, the speed of reaction is to “stop the crisis.” The most important thing is “bleeding”. Of accuracy. As the crisis shifts from “response” to “recovery” and “rebuilding”, it becomes important to start thinking about how the company can get back on its feet and how it can build a more effective cybersecurity foundation for the future.
For David Mahdi, a good IAM program is like a refueling team that strikes the right balance between the importance of getting the rider back on the right lane quickly (speed) and making sure the wheel does not slip, and not detached midway (accuracy).
To give the organization “speed of survival”, David Mahdi recommends prioritizing the implementation of secure remote access, Unified SSO and Multi-Factor Authentication (MFA), with a fast and “good enough” approach to IAM and CIAM (Client Identity and Access Management). Then, to maintain accuracy, the organization needs to focus on protecting accounts, detecting fraud, managing privileged accounts, and moving to a low-cost SaaS mode.
“If you don’t use premium account management tools, technology, people, and processes built into the fabric of your organization, now is the time to do so. Why? Because the bad guys are going after the superusers. Their accounts have access to your sensitive data, and they have access to your kingdom’s keys. And that’s what it is.” You really want to protect him, “sums up David Mahdi.
In another presentation titled “Deconstructing the Twitter Attack – The Role of Premium Accounts,” Matt Tarr, solutions engineer at CyberArk, discussed the social engineering attack on Twitter that was carried out over the summer that led social media users to defrauding nearly $ 121,000 in coins. Bitcoin. For him, “user training in.”
Security basics, and premium account management can slow down or even prevent all of this.
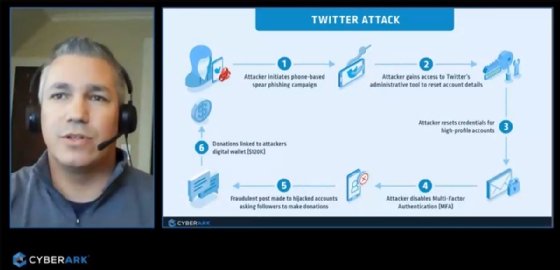
To clarify, “This attack highlights the risks of unsecured privileged accounts. It should remind us how quickly an identifier or identity can become unique under certain circumstances. Without proper security, attackers – external or internal – can use it to unlock critical assets. , Either with a domain administrator or a simple support account who can make changes to the Twitter profile.
Matt Tarr notes in passing that the said attack was not particularly complex: “Originally, it was thought to be the work of experienced attackers of a nation-state. But now it appears to have been carried out by a relatively undeveloped group of hackers, motivated by financial gain and / Or wonderful aliases. “
For him, the incident made it clear that it was easier for the attackers to hack into Twitter itself than to gain control of a user account with MFA. The attack started with a phishing or phishing campaign targeting specific Twitter employees.
Once the attackers gained access to the employee’s credentials, they gained access to Twitter’s administrative tools and were able to disable the MFA on several high-profile accounts. Since Twitter did not have adequate security controls around these administrative tools, the attackers were able to misuse them unnoticed. In short, Matt Tarr sums up, Twitter has protected its users’ accounts better than those of its admins.
Against social engineering attacks of this kind, he recommends raising awareness and training employees, using strong passwords, but also giving priority to managing premium accounts and implementing security rules. Conditional recourse to the State Department.
In another session titled “The Security Leader’s Guide to Managing Premium Access,” Felix Gitgens, Director of Research at Gartner, explained that managing premium accounts is an important part of any security program due to expanding IT environments, and hence the growing strength of premium accounts, management tools, and other critical elements such as Encryption keys And certificates.
So Felix Gitgens recommends that organizations put in place strict controls on premium accounts, starting with limiting the total number of premium personal accounts, adopting more shared accounts, and reducing the terms and hours over which high privileges are granted.

“Certified tv guru. Reader. Professional writer. Avid introvert. Extreme pop culture buff.”





More Stories
AI-powered traffic lights are now being tested in this city in Baden-Württemberg.
The use of artificial intelligence in companies has quadrupled
AI Startup: Here Are Eight Startup Ideas