summary
brodotIt is a tool for visualizing malware behavior developed by Christian Vogner, a member of the Austrian Computer Emergency Response Team (CERT).
It is released under the International Study Center (ISC) license, and the software can be downloaded for free from the website.
ProcDot can integrate and visualize information obtained from process monitoring and packet capture tools used in malware analysis.
Process Monitor is an advanced Windows monitoring tool published by Microsoft's Sysinternals that allows you to monitor file systems, registry, process activity, etc.
Packet capture tools are tools used to visualize communications of different protocols.
In malware analysis, we combine these tools to analyze the behavior of malware inside a computer and its communications with the outside world.
However, the process monitor cannot capture network-related information, and packet capture tools cannot identify which process is communicating.
ProcDot is a utility that integrates and visualizes the information obtained from these two types of tools.
In addition, many logs obtained from these tools are unrelated to malware operations. This information can be filtered to display only the behavior of the malware.
How to use it in malware analysis
This section provides the steps that should be used to analyze malware.
Also in this tutorial, we will use Wireshark as a packet capture tool.
- Get records
- Initial settings for ProcDot
- Run visualization
- How to read a chart
Detailed steps
1. Get the record
To use ProcDot, you need CSV logs obtained from Process Monitor and pcap logs obtained from Wireshark.
The malware executes in an environment where Process Monitor and Wireshark are running, and two types of logs are obtained.
At this time, you need to change the process monitor settings as follows.
- Disable “Filter > Enable Advanced Output”
- Select “Export all events” when exporting logs
2. ProcDot initial settings
ProcDot requires some third-party software to run.
- Windump (for Windows)/Tcpdump (for Linux)
- graphviz
Download these programs in advance and record the paths to the necessary files when you start ProcDot for the first time.
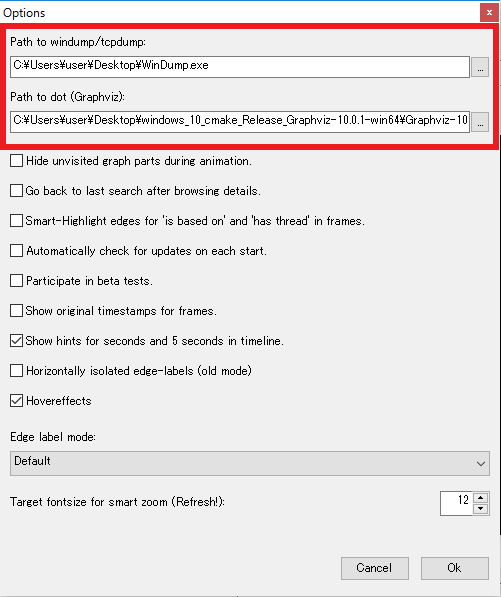
Also, depending on the environment, when you register Windump, an error may appear stating that wpcap.dll is missing.
In this case,Win10pcapPlease try to install.
3. Implement the visualization
This is the basic screen of ProcDot. Enter Process Monitoring and Wireshark logs into the Monitor Logs field at the top of the screen.
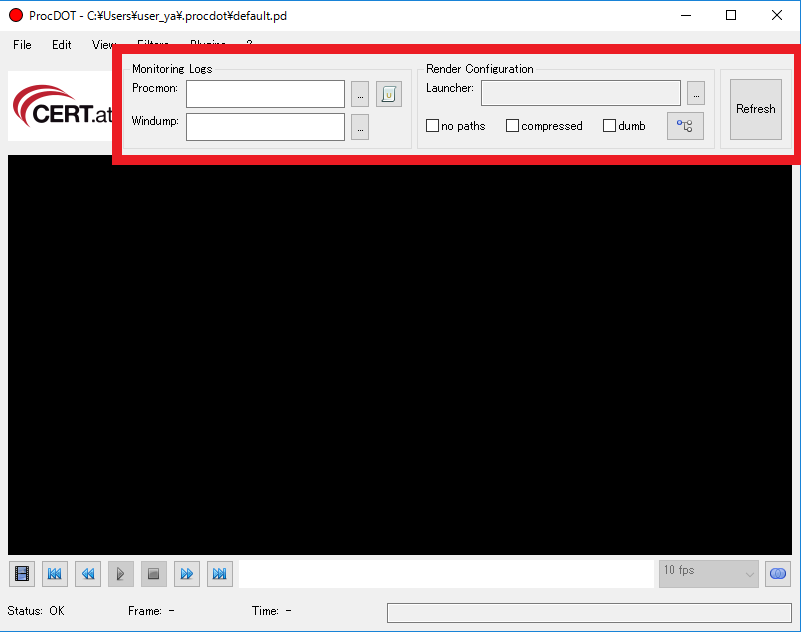
Next, select the operation you want to render from “Render Configuration”.
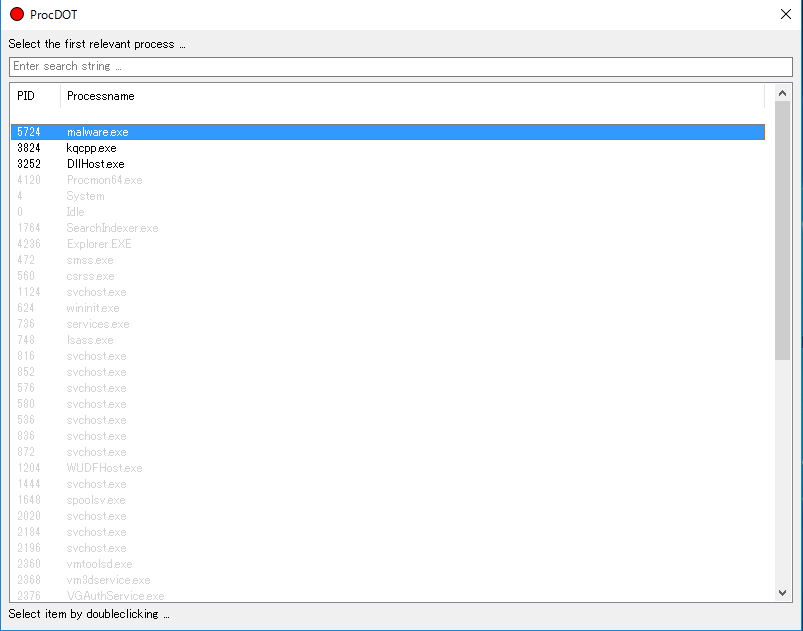
Finally, press “Update” to draw the graph.
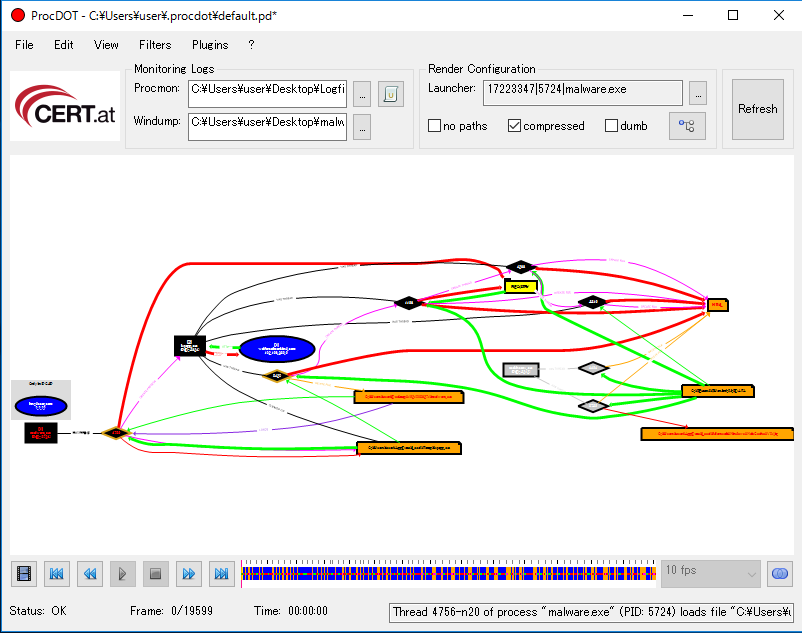
4. How to read a chart
The following image is an enlarged portion of the chart above.
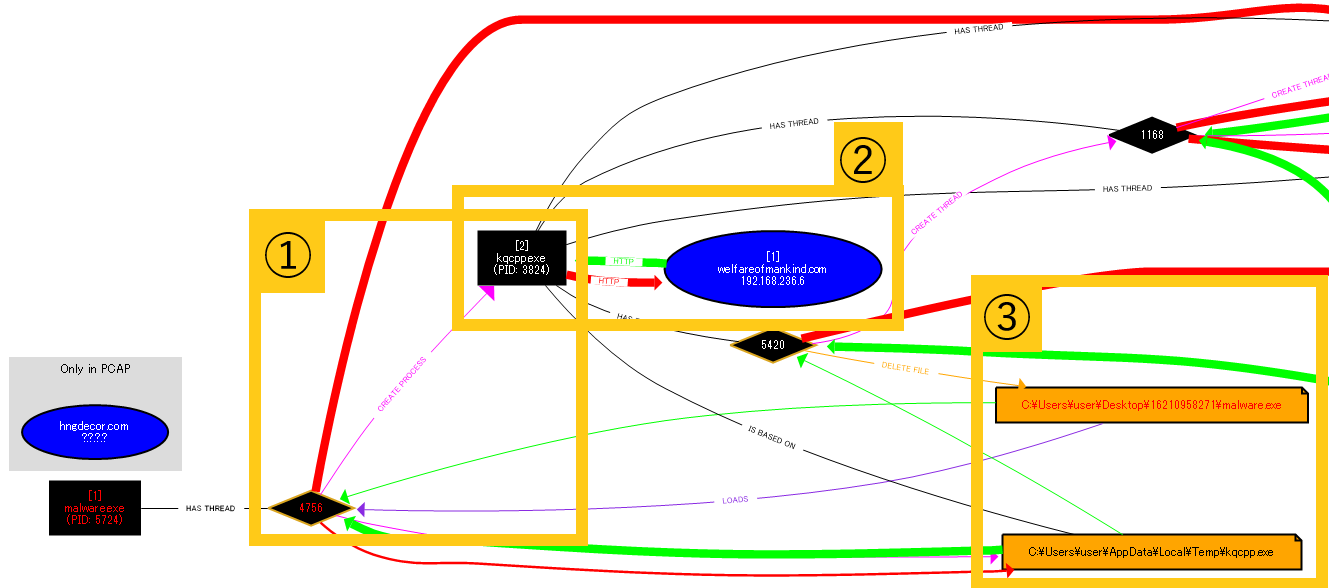
The image shows what Malware.exe (PID: 5724) does. In ①, the thread created by Malware.exe (PID: 5724) creates the subprocess kqcpp.exe (PID: 3824). Also, in ②, kqcpp.exe (PID: 3824) is a malicious URL, which is human welfare.[.]We are communicating with com.
The two orange icons inside the ③ rectangle are files created or deleted by the relevant processes. Arrows depict the process that performed which operation.
In this way, the graph displays a combination of information obtained from monitoring processes and information obtained from a packet capture tool.
Although not shown in the picture, in addition to the above items, you can also visualize log writes and deletions, injections by operations, and so on.
ProcDot also has some useful features.
- Ability to reverse the schedule on the chart
- A function that works with Wireshark to display the TCP flow for the corresponding packet.
- Ability to view an overview of files and registry

“Travel maven. Beer expert. Subtly charming alcohol fan. Internet junkie. Avid bacon scholar.”





More Stories
The ranking of the best survival horror games selected by the IGN US editorial team has been released! Resident Evil RE:2 ranked first
Enjoy a hot cigarette while looking at whales and tropical fish under the sea ⁉︎ “Ploom Dive” is an amazing spatial video experience using Apple Vision Pro
Apple Watch now supports sleep apnea, watchOS 11 released – Impress Watch